Latest from our business, security
and technology blog
Search the blog:
2024 Tech Year in Review: Innovations, Challenges and Lessons Learned
As we wrap up 2024, the tech industry has once again demonstrated its dynamic and ever-evolving nature. From advancements in cybersecurity to breakthroughs in artificial intelligence, this year has been a journey of growth, challenges, and transformative lessons.
Guide: Cyber Security Training - Your Best Defence
Cybercrime continues to evolve, and small and medium-sized businesses are some of the biggest targets. With fewer resources dedicated to security, these organisations are often seen as easy prey for cybercriminals.
10 Reasons Why you Might Not Be Receiving Emails in 2025
Email remains an essential communication tool in both personal and professional settings but despite continuous advancements in technology, a range of issues can still disrupt the smooth delivery of emails.
Impersonation in Action: How Fake IT Support Threatens Your Security
In the world of cybersecurity, there are few threats as deceptively simple yet devastatingly effective as social engineering. These attacks exploit the human element - tricking individuals into granting access, revealing sensitive information or performing actions that compromise their...
Broadcom's Acquisition of VMWare: What It Means for Customers and Why You Should Consider Azure or AWS
In a significant development within the tech industry, Broadcom's recent acquisition of VMWare has sent ripples across the market. While mergers and acquisitions often promise enhanced capabilities and expanded offerings, they also bring about changes that can significantly affect customers.
5 Best Tips to Keep Your Device in Check
In our increasingly digital world our devices are central to productivity, creativity and staying connected. However, wear and tear, software glitches and cluttered storage can slow your PC down over time making it less efficient.
Why Consistent Email Signatures Matter - and How to Achieve them
In today’s professional world, first impressions often happen online - and email remains a core part of that communication. For most companies the email signature is more than just contact details, it’s a direct representation of your brand. But when email signatures are inconsistent across an...
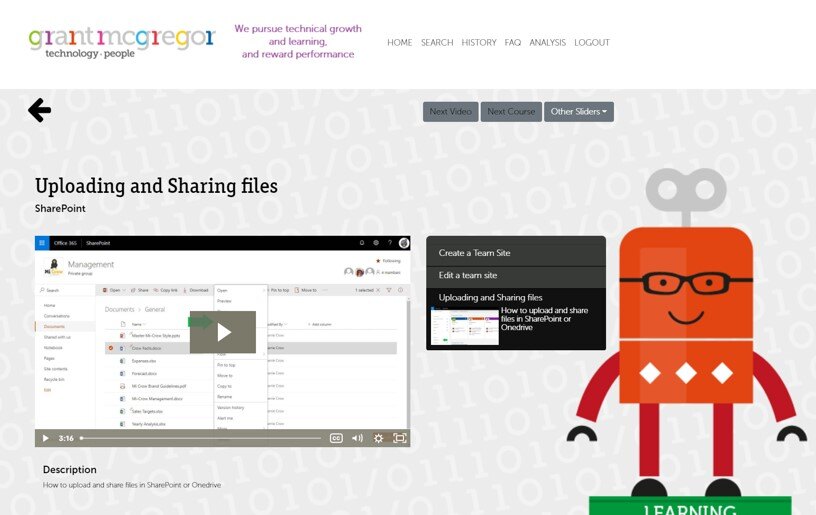
Empower Your IT Skills Through Micro-Learning
Empower your team with the flexibility and knowledge they need to grow. Learn how bite-sized videos can help you stay ahead in the fast-paced tech world. Boost your professional career, enhance productivity and make your daily tasks easier to manage with Grant McGregor's education portal.
How AI Can Help with Email Overload
In the modern workplace, email remains one of the primary modes of communication. However, the sheer volume of emails received daily can quickly become overwhelming, leading to decreased productivity and increased stress. Enter AI-powered tools like Copilot, designed to help manage email overload...