The Dark Web: What It Is, What It Isn’t and What You Need to Know
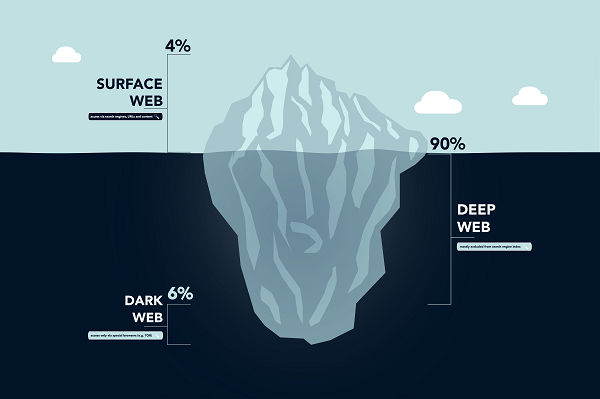
The dark web is known as a place where criminal activity takes place online – the refuge of weapons dealers, drug dealers and other nefarious activities. While your first response might be that it is nothing to do with you, it isn’t something that IT leaders can afford to dismiss out of hand. Here’s what you need to know.
The Internet is a vast virtual world in which billions of searches take place every day. Many of these are conducted via search engines, such as Google. This is the surface web: a collection of indexed sites designed to be found via the search engines.
It offers you the information and services you use every day. Your organisation uses it to show its public face to the world via its website. And you use it to access news, shopping and other online resources.
The surface web vs. the deep web
But the surface web is just the tip of the iceberg. Beyond this is a vast realm of unindexed websites that won’t be indexed or found by search engines like Google. This is the deep web.
Most of the deep web is also fully above board. It is the content that sits behind passwords or web forms and that isn’t designed to be accessed by the search engines. Usually, this is done to protect personal or sensitive data. It includes things like in-review blog posts, email and social messaging accounts, private organisational databases and intranets, and academic journals. This vast swathe of web pages constitutes the bulk of the Internet: the huge hulk of the iceberg that exists below the visibility of the surface.
However, part of this deep web, the unindexed part of the Internet, is much more nefarious. It’s a place that is inaccessible to traditional browsers – thanks to its unique registry operator. To access it, you’ll need a specialist browser such as Tor. Even then, its content is protected behind firewalls, encryption, close supervision and a randomised network infrastructure. This is the dark web: an anonymised and encrypted area of the Internet where a collection of websites have been created but deliberately concealed.
It’s not hard to understand why the dark web lends itself to criminal activity.
How cyber criminals use the dark web
A good overview of how cyber criminals use the dark web is provided in the 2017 Cybercrime: understanding the online business model(1) report from the UK’s National Cyber Security Centre. It discusses how organised criminal groups share similar techniques and services and communicate with each other over the dark web in order to collaborate and advertise new services, tools and techniques.
More recently, GCHQ published a paper in February 2021 on the potential of AI, particularly in pioneering a new national security approach(2). It highlighted how criminal groups use the dark web for a range of serious criminal activity – from ransomware attacks to human trafficking. These groups often trade with cryptocurrencies, such as bitcoin, so that their financial transactions are as anonymous as their dark web activity. GCHQ plans to use its artificial intelligence (AI) capabilities to clamp down on these serious crimes and organised criminal groups.
However, it is worth noting that it isn’t only criminal groups who use the dark web. The dark web was originally conceived by the US government, which realised that the openness of the Internet could jeopardise covert activity. It developed as a safe space for spies to communicate.
Today, it is used by journalists to communicate with political activists and whistle-blowers who require a similar degree of anonymity.
What do you need to know about the dark web?
Users of the Internet have little cause to use the dark web. When using regular search engines like Google they have a degree of protection because they can be assured that they won’t stumble across dark web sites. However, the use of anonymised web browsers like Tor has increased among general users, which opens the possibility of inadvertently (or otherwise) accessing the dark web.
As an IT leader it is best practice to discourage users from accessing the dark web. In the same way that in the real world we wouldn’t purposefully seek out and travel to areas of known criminal activity, users should not do so in the virtual world.
Users need to understand that it isn’t just the sale of malicious software that is made possible by the dark web. The dark web itself is littered with malicious software placed to take advantage of unsuspecting users. Nor is it immune to phishing scams. It requires just as much caution as regular Internet use – more so, because a greater proportion of the activity there is criminal in nature.
While regular users should avoid the dark web, there are legitimate reasons why an IT specialist might want to use it.
Constella’s 2020 Identity Breach report(3), as shared in Security magazine(4), found that more than 18 billion raw identity records are being passed around underground marketplaces on the dark web. It emphasises that organisations need to be alert to such breaches, so they can take remedial action as soon as possible.
Furthermore, understanding the cyber tools and malicious code that is available for purchase on the dark web is an important part of preparedness in any cyber security defence. To mitigate the risks, you need to know what the risks are.
While these might seem like legitimate reasons to traverse the dark web, we would still urge caution. Far better, instead, to leave such research and monitoring to specialist security agencies. By using a third party to monitor leaked data and emerging threats, you create a buffer between you and the criminal activity that is so prevalent on the dark web.
What should IT leaders do to mitigate the threat?
As the NCSC points out, it is important to be aware of the extent of the online criminal ecosystem that supports and enables cyber attacks and the business model behind them.
It is important that all organisations have processes and partnerships in place, so that they know – via swift alerts – when data has been compromised.
IT leaders need to put processes in place to respond when data is compromised. This requires an understanding of data flows within and outside of the organisation, especially when it comes to identities and credentials. Make sure you will be alerted swiftly if these are compromised: resetting credentials, locking down networks, and monitoring for further suspicious activity.
Of course, the best way to respond to these threats is to try to prevent leaks in the first place. Cyber Essentials is a good starting point. User education is also key. Encourage users to use unique and complex passwords for all their accounts. Keep information sharing online to a minimum. Use separate accounts for users and administrator activity. Adopt a policy of least privilege. And err on the side of caution, whatever you are doing online.
If you’d like further advice or information about any of the issues or tools mentioned in this blog, please reach out to the Grant McGregor team. We’re always on hand for advice or information.
You can reach us below:

Sources:
1. https://www.ncsc.gov.uk/news/ncsc-publishes-new-report-criminal-online-activity
2. https://www.gchq.gov.uk/artificial-intelligence/index.html
3. https://info.constellaintelligence.com/2020-identity-breach-report
4. https://www.securitymagazine.com/articles/94951-what-you-need-to-know-about-the-deep-and-dark-web




