Latest from our business, security
and technology blog
Search the blog:
10 Reasons Why you Might Not Be Receiving Emails in 2025
Email remains an essential communication tool in both personal and professional settings but despite continuous advancements in technology, a range of issues can still disrupt the smooth delivery of emails.
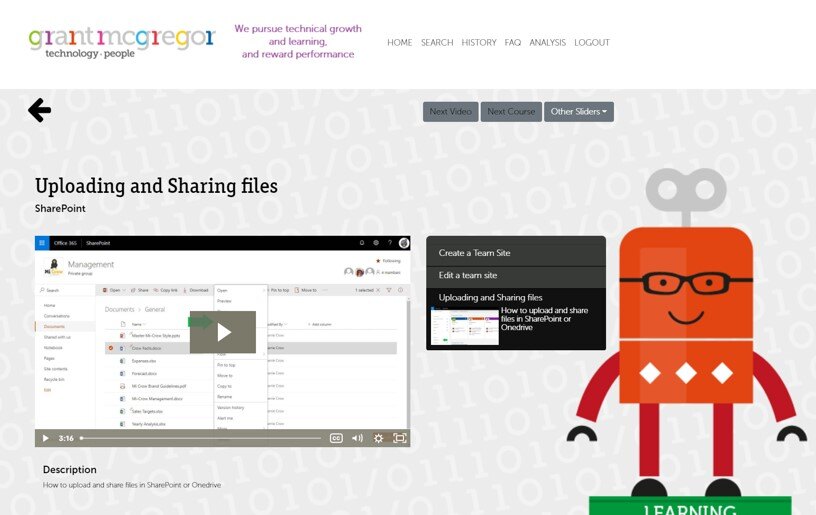
Empower Your IT Skills Through Micro-Learning
Empower your team with the flexibility and knowledge they need to grow. Learn how bite-sized videos can help you stay ahead in the fast-paced tech world. Boost your professional career, enhance productivity and make your daily tasks easier to manage with Grant McGregor's education portal.
Celebrating Wellbeing Champions in the Tech Era
At Grant McGregor, we’re excited to sponsor the Wellbeing Champion Award at the 2024 Scottish Gymnastics Awards for the second year in a row!
The CrowdStrike outage explained for business owners and managers
On Friday 19th July 2024, a routine software update from CrowdStrike, a leading cyber security company, caused a major issue affecting an estimated 8.5 million Windows computers.
New ranking for Grant McGregor in 2024 international MSP awards
Grant McGregor has been named as one of the top-performing managed service providers in the prestigious 2024 Channel Futures MSP 501 rankings. The Channel Futures MSP 501 list, a technology industry benchmark, ranks companies based on their growth, profitability and innovation.
What can we learn from the Post Office Horizon scandal about how to choose an IT partner?
One of the biggest miscarriages of justice in British legal history was driven by a faulty computer programme. Made worse by the supplier and procurer of the system refusing to accept that it was at fault, the scandal has finally got the recognition it deserves following an ITV drama about the...
2024 Tech Predictions: What cyber security challenges will we be facing in 2024?
Here’s our roundup of the cyber security challenges about which leading organisations in this space are warning for 2024. Pulling information from a variety of expert sources, this covers some of the cyber security preparations you’ll need to be considering this coming year.
The technologies and tech stories that will set the agenda in 2024
What are the news stories that will be dominating the tech press in 2024? The Grant McGregor team dusts off our crystal ball to make some predictions. Tech made the headlines in 2023, with news about generative AI taking much of the column space. We think it will be dominating the 2024 agenda too...
The biggest tech stories of 2023: Our recap of a game-changing year
There is no doubt we’ve seen some huge tech news over the last 12 months. The Grant McGregor team looks back and reflects on some of the biggest stories from 2023. From cybercrime to new product launches, here’s our pick of five of the biggest tech news stories from 2023.