How to Protect Your Business Against Cyber-Attacks and Data Theft
Wow! Quite a weekend of news around Cyber Security...
This was an article we had written a couple of weeks ago now and had scheduled for publication today just for the sake of offering our readers and supported end-users ongoing education about cyber security and playing your part...
However, events since Friday and over the weekend have heightened the public sense of vulnerability to Cyber 'attacks' and the need for an ongoing program of measures and counter-measures to combat the evolving cyber threats.
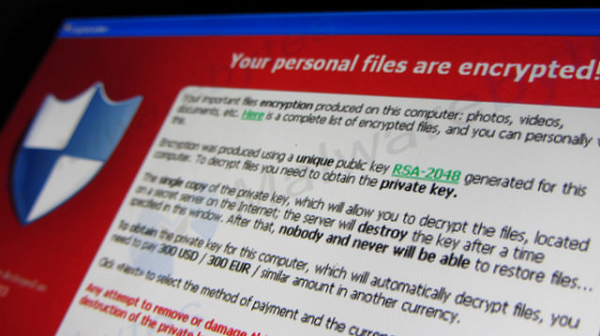
We have all now witnessed the very public examples of the NHS trusts, companies and individuals who have become victims of cyber attacks in the form of a ransomware encryption of their data. In the case of the NHS, sadly it has had a very real effect on patients, operations and care.
In this case, the 'attack' seems to have been a combination of a targeted attack against un-patched systems (that should have been updated to combat known system vulnerabilities) plus a lack of human awareness of the nature and style of the 'triggers' to the threat - typically borne by emails with 'malicious' attachments and/or web links that, when clicked, enable the encryption of the hard drives and the data contained on them. However, then configured to quickly spread via a type of malware called a 'worm'.
There are all sorts of arguments that are being made to say how this series of events might have been prevented - the NSA's detection of software vulnerabilities not being shared quickly enough; running unsupported systems such as Windows XP that have no more security updates being issued; the relevant patches or security updates not being applied quickly or rigorously enough; lack of funding for infrastructure and so on.
An effective patch management system combined with effective, layered cyber defences around data to provide strong protection against malware strains and evolving (so-called zero-day) threats are but some of the key measures that the Government's own National Cyber Security centre have recommended to improve defence against these truly nasty and harmful threats.
Add to that having a reliable back-up of data and systems with fast recovery methods that are tested to be ready for the worst-case scenario; plus finally, good old common-sense by computer users to be vigilant for unexpected or suspicious emails, links and attachments!
One valuable and inexpensive way of thoroughly checking that your organisation has these key measures reliably in place is to get tested and accredited for the Government Cyber Security standard called Cyber Essentials.
You can find out more about how to get tested here. Keep safe everyone!
Here's the original blog post below...
The rise of computing to dominate how we do business in the 21st century has brought a myriad of benefits to businesses of all shapes and sizes, solving almost all logistical and entrepreneurial restrictions that have plagued businesses for centuries.
Instant communication, infinite databases and data mining are just three examples from thousands of how computing has revolutionised business and unlocked the true potential of every industry – not to mention creating many more industries from scratch. Like all ‘magic bullets’ to our problems, however, computing has not been without risk.
Or casualties.
A single email worm (a type of computer virus) known as MyDoom has so far claimed $38.5 billion in damages to businesses since it was unleashed in January 2004. Threats to businesses include data breaches where hackers steal information on your business or customers to sell online, ‘ransomware’ which remotely holds your computer and its data hostage until a ransom is paid to the hacker and ‘phishing’ which uses fake emails to deceive the recipient into providing confidential information.
Cybercrime is increasing at a rapid rate as well.
From 2014 to 2015, cybercrime attacks increased by a whopping 38%. By 2019, the cost of cybercrime to businesses is expected to reach $2 trillion per year , which is four times what it was in 2015.
With such a range of threats that are increasing in severity and frequency, how can a business defend itself against such attacks?
Believe it or not, one of the most effective defences against cybercrime is simple staff training. This is because the hacker’s most useful, powerful and prolific tool to breaching a company is not a complicated virus or a state-of-the-art piece of technology. It is something that criminals have been using since the dawn of time.
Social engineering.
Social engineering (also known to hackers as ‘people hacking’) is the art of deceiving people into giving away important information or access via verbal or written communication.
This can be done by a hacker, for example, who has dressed himself up as a technician and who walks into the reception of a building and claims to have been sent by an IT company or even the victim’s own company to fix a ‘server issue’ or another vague fault.
If the receptionist does not take his word for it and allow him into the site right away, the hacker will act annoyed that they are being kept waiting, pressuring the receptionist to let them get on with their ‘job’. This may sound like a farfetched method, but you would be shocked how often this works.
Receptionists will hand over a visitor pass, the hacker will stroll into the building, find an open access point and directly upload viruses to a network through that access point or just download what they need there and then. They can also then install rootkits or other backdoors into the network for next time they want to launch an attack.
In its most simple form, hackers may literally just wait outside a door until an employee walks through and then follow them in whilst striking up a conversation.
Sound impractical?
Colin Greenless from Siemens Enterprise Communications dressed as a delivery driver and stood outside the front door of a major FTSE financial services firm and then followed an employee through a secure door when it opened. He did this again and again, making his way to a major server room.
Seeking a larger challenge, he then set up in a meeting room on the third floor for three entire days. From this room he pretended to be a member of IT staff and made many internal calls to other areas of the building asking for personal data that the ‘IT department needed’. 17 out of 20 of those he called complied, giving him total access to their electronic data and often that of their whole department.
Fortunately, Colin Greenless was doing this as a social experiment and as a clear demonstration of the need for security training, so no actual damage to the company was caused. Colin was one of the good guys.
This is not the case most of the time, as many companies have found out to their peril.
This shows why training your staff is often the cheapest, easiest and yet most effective defence against cyberattacks.
Staff who know not to allow strangers into a building or give over personal information over email or phones and report such strange behaviour will act as informal security at all times.
Other devastating types of social engineering attacks include infected hardware being plugged in by unsuspecting employees. Hackers will leave USB sticks with viruses on in public places in the mornings, waiting for people to pick them up on the way in to work and plug them in at the office out of curiosity. Without them clicking anything or perhaps even without them knowing, viruses swarm from the USB stick into the computer network.
Hackers may also give out free CDs in the street claiming that they have music on, whereas it’s really just a nasty bit of malware. Company rules (and defensive technologies) against plugging in unauthorised hardware will go a long way to defend against this. Some companies opt to have USB ports locked shut with an installed panel which can only be opened by authorised IT staff, though this is uncommon and in some cases impractical.
Apart from teaching staff to recognise and avoid social engineering tricks, you can also prevent cybersecurity attacks by making sure that you have multiple layers of defences around your systems.
This includes having up-to-date antivirus and antimalware applications or services. The ‘best’ antivirus software changes from month to month and year to year, but a quick search online will show who is worth investing money into. For home or personal use, free or low-cost antivirus software such as Malwarebytes could be sufficient. For business purposes, though, it is always best to have a fully-paid premium defence or anti-malware service in place.
Keeping all of your computers, operating systems and other software up-to-date is also vital so that any exploits or security flaws are patched as quickly as possible. Encrypting your WiFi connection and making sure there are no open remote access points will also go a long way to prevent a remote attack from hackers who are nearby with packet-sniffing kits or other remote break-and-enter capabilities.
And let’s not forget our easy-to-crack, simple passwords that we re-use across the web that a hacker can break in no time at all. Never use or leave default passwords in place on hardware, opt for a strong, 3-dimensional password structure, or better still a 2-factor Authentication app that will need a one-time secondary token or code to access your data and systems.
Finally, have a plan for the worst-case scenario.
Having data loss prevention software and, should the worst happen, a plan for disaster recovery is vital. Make sure that if something does go wrong then you know what to do. A data theft is different from a bank robbery in that it can sometimes be weeks or months before a company realises that it has been breached. As soon as you realise that an attack has taken place, you already need to know what you are going to do and when.
Consulting an IT security professional about this for your particular company is advised and helpful. If your company has its own IT staff or department, make sure they have a plan in place.
If you are interested in finding out how vulnerable you are then you can actually hire someone like Colin Greenless to test your defences remotely, in person or both. This is known as penetration testing, when White Hat (aka ‘good guy’) hackers will break into your company for you and then let you know how they did it so that you can better protect yourself in future.
You should also get tested for the UK Government’s own security accreditation; Cyber Essentials, which examines the fine key areas of security that are behind around 80% of all breaches. Find out how to qualify for Cyber Essentials here.
One thing is for certain – doing nothing and hoping for the best is the first step on the path to your company becoming an IT security statistic. By making changes early you can avoid or mitigate a disaster before it happens.
Next steps?
A surprising amount of companies and organisations are still failing to cover even the most basic security management best practices adequately such as security patch management and password policies.
Find out how becoming properly accredited for the UK Government’s Cyber Essentials scheme can highlight and help you to fix any shortcomings you have with IT and data security.
Get in touch with our Cyber Essentials UK team on 0808 164 4142.
Photo credit: christiaan_008 via Foter.com / CC BY-SA




