Latest from our business, security
and technology blog
Search the blog:
5 Things Every BYOD Policy Needs
Bring Your Own Device (BYOD) policies are rapidly gaining traction in the modern workplace owing to the flexibility and convenience they provide to both employees and their employers.
6 Things You Can Do This Year to Boost Your IT Performance in 2018
We take a look at six simple things you can do this year to boost IT performance and productivity in 2018.
The Two New IT Vulnerabilities that Affect Nearly Everyone
You’ve probably heard of Spectre and Meltdown by now – the two new vulnerabilities that researchers have identified as affecting chips from Intel, AMD and ARM. We take a look at the risk they pose and what you should be doing about them.
New Year... New IT Partner?
Technology isn’t the starting point for many small businesses and start-ups – unless technology is your business.
The Beginner's Guide to Cloud Security
As increasing numbers of businesses shift their workloads to the cloud, the security threat we face is changing. Where our data goes, the hackers follow – and now cloud attacks are on the rise.
Protect Your Business from Insider Attacks
When we discuss cyber-attacks it often refers to those that come from the outside – the ones that are typically high profiles cases, such as malware, hacking, DDOS and ransomware.
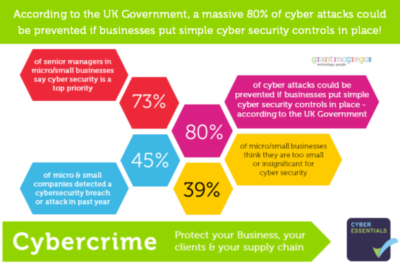
The Impending SME Security Crisis
The brutal fact is most small businesses are not spending enough time or money on cyber security – leaving them exposed to ransomware, severe regulatory fines, reputational damage and lost business opportunities.
You’re Not Too Small to Be a Victim: The Obvious IT Security Fails Small Businesses Can Avoid
The Rise of Personally-Targeted Spear-Phishing Attacks & How to Defend Yourself From Them...
As we all become more wary about the tell-tale signs of a phishing email attack, criminals are turning to a more targeted approach to email scamming: the spear-phishing attack.